Synopsis: A simple but malicious subtitle file can be used to gain control of your PC, TV or smartphone. Check Point researchers have spotted vulnerabilities in VLC, Kodi, Stremio, and Popcorn Time in the way these media players handle subtitle files. As of now, fixes have been released for the media players.
According to a blog post published by Check Point security, a subtitle file could be modified to create a new attack vector and compromise the devices such as PCs, mobile devices, TVs, etc running vulnerable media players. Once compromised, the attacker can perform remote code execution, steal data, use the device as a pawn in a DDoS attack, and more. The researchers say, delivering a cyber attack when subtitles are loaded onto a media players is a “completely overlooked technique”.
Most of the people download subtitles files from repositories on the web without giving a second thought, treating them as no more than innocent text files.
The researchers say that attackers can upload a malicious subtitle on a repository and manipulate the rankings to put their results on the top. This could result in an increase in manual download counts and automatic download counts (by media players).
They also note that subtitles aren’t considered as a threat in comparison to traditional attack vectors which are well-known to security companies and users. That’s the reason a malicious code hiding in a subtitle file could easily sneak through filters deployed by antivirus software.
The actual vulnerability lies in the way the media players handle subtitle files. One aspect that contributes to the complexity of the whole thing is a large number of subtitle formats each having its own set of features. Currently, there are around 25 subtitle formats in circulation.
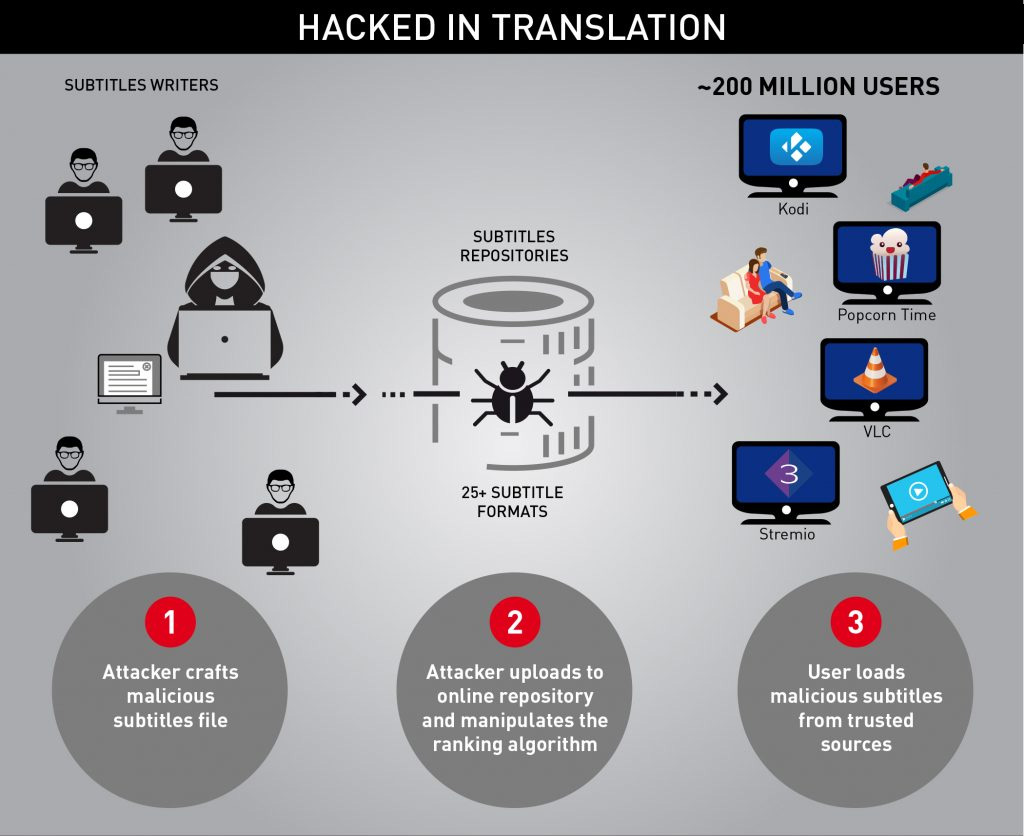
Different media players have their own method of parsing and combining different subtitle formats in order to enhance user experience. As a result, the researchers were able to find distinct vulnerabilities in affected media players.
The list of affected media players includes VLC, XBMC Kodi, Popcorn Time, and Stremio. However, the researchers don’t exclude the possibility of the exploit existing on other media players. The researchers haven’t published further details as the developers are currently investigating the vulnerability.
Each of the affected media players has millions of users with VLC topping the list. The last release of VLC (June 5, 2016) has been downloaded more than 170 million times. In total, the researchers estimated that around 200 million devices running the affected media players are exposed to the attack.
DOWNLOAD SUBTITLE HACK FIX
Check Point researchers contacted the developers of the affected media players in April 2017. Thankfully, the security patches have been released.
In the case of VLC, the attacker can leverage memory corruption bug. The media player had four vulnerabilities (CVE-2017-8310, CVE-2017-8311, CVE-2017-8312 and CVE-2017-8313) which have been fixed by VideoLan.
A fix for VLC is available as the latest Version 2.2.5.1 which is present on the VideoLan’s website. The same is the case of Stremio.
The developers of Popcorn Time and Kodi have created a fix, but it’s not released for public yet. For Popcorn Time, you can download the fix manually using this link provided by the researchers. Head over to GitHub where you can find a source code fix for XBMC Kodi.







