Apple has released iOS 9.3.5 update for iPhones and iPads to patch three zero-day vulnerabilities after a piece of spyware found targeting the iPhone used by a renowned UAE human rights defender, Ahmed Mansoor. One of the world’s most invasive software weapon distributors, called the NSO Group, has been exploiting three zero-day security vulnerabilities in order to spy on dissidents and journalists. The NSO Group is an Israeli firm that sells spying and surveillance software that secretly tracks a target’s mobile phone.
The zero-day exploits have allowed the company to develop sophisticated spyware tools that can access the device location, contacts, texts, calls logs, emails and even microphone.
Apple fixed these three vulnerabilities within ten days after being informed by two security firms, Citizen Lab and Lookout, who conducted a joint investigation.
Background Story: Malware Discovery
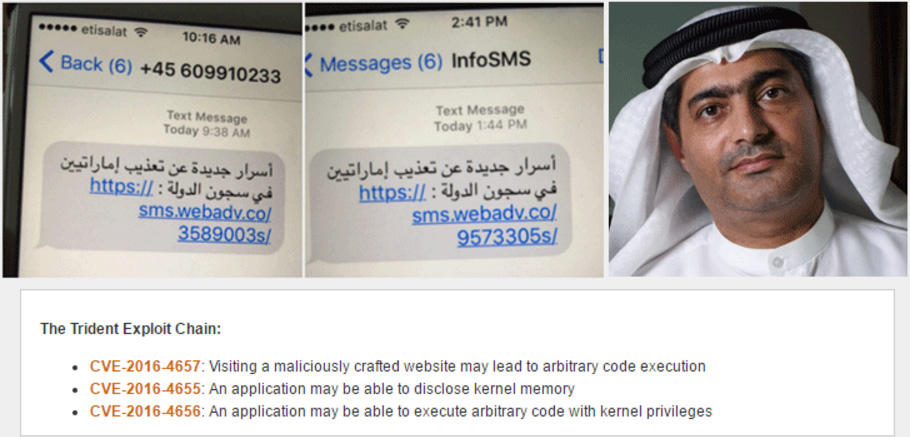
Mansoor, 46, ‘Martin Ennals Award’ winner from the United Arab Emirates, received a text message on his iPhone on August 10, from an unknown number. Mansoor found the message suspicious and knowing that government hackers had already targeted him in the past, he forwarded that message directly to Citizen Lab researcher Bill Marczak. Citizen Lab brought in Lookout, a San Francisco mobile security company, to help examine the message.
After analyzing the message content, the researchers found that the link led to a sophisticated piece of malware that exploited three different unknown flaws in Apple’s iOS that would have allowed the attackers to get complete control of Mansoor’s iPhone.
Those links, if clicked, “Mansoor’s iPhone would have been turned into a sophisticated bugging device controlled by UAE security agencies,” the Citizen Lab explained in a blog post.
“They would have been able to turn on his iPhone’s camera and microphone to record Mansoor and anything nearby, without him being wise about it. They would have been able to log his emails and calls — even those that are encrypted end-to-end. And, of course, they would have been able to track his precise whereabouts.”
Those links, if clicked, “Mansoor’s iPhone would have been turned into a sophisticated bugging device controlled by UAE security agencies,” the Citizen Lab explained in a blog post.
“They would have been able to turn on his iPhone’s camera and microphone to record Mansoor and anything nearby, without him being wise about it. They would have been able to log his emails and calls — even those that are encrypted end-to-end. And, of course, they would have been able to track his precise whereabouts.“
According to a blog post published by Lookout, the three zero-day flaws, dubbed “Trident” by the firm, involved:
- A memory corruption vulnerability in WebKit that could allow hackers to exploit a device when a user clicks on a malicious link.
- Two kernel bugs (allowing device jailbreak) that an attacker secretly installs malware on victim’s device to carry out surveillance.